For a customer I configured Device certificate check on a Netscaler VPX 11.0.65.72 based on CTX200290 in combination with Windows 2012 R2 Online responder service. The EPA check failed and access was denied
- I configured the OCSP responder with the correct URL (same as device certificate and resolvable on the NS)
- I opened up port 80 for NSIP to the intermediate CA
- I bound the OCSP to the intermediate certificate (which is the certificate provider)
- I configured the ‘enable device certificate’ on the Vserver gateway
- I added the CA and the intermediate CA certificate to the Vserver gateway with the latter for mandatory certificate check
- I also loaded the Netscaler Gateway plug-in as recommended since this plug-in is able to connect to the local machine certificate store (as the EPA plug-in runs in user context and cannot).
So far I ended up with only an ‘access denied’ because of failed security requirements on the posterrorepa.html page. I checked the %AppData%\Local\Citrix\AGEE\nsepa.txt for further troubleshooting. This text file suggested the Netscaler Gateway plug-in took over from EPA plug-in and checked for the presence of the certificate successfully. It’s the contact with the Netscaler or check from the OCSP responder which failed.
I finally got it working after a long day of research, trial and error! So far the prereqs to get this working are:
- Disable NONCE on the OCSP responder on the Netscaler and tick the Trust Response box on the OCSP responder on the Netscaler
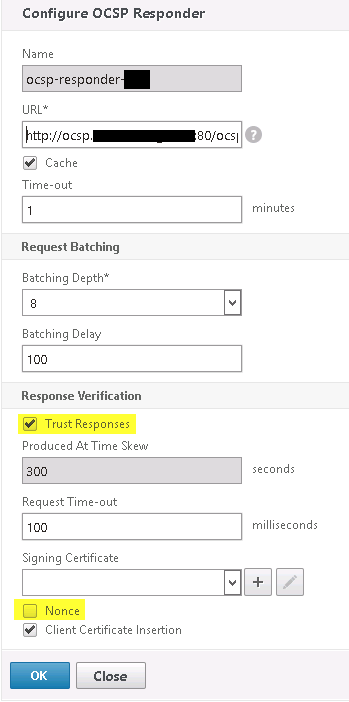
A OCSP client request with Nonce enable and with NONCE disable at the MS Online Responder will be treated as an unauthorized request. As stated in this MS Technet Article:
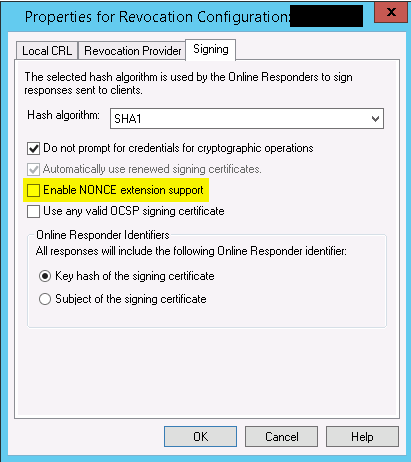
Enable NONCE extensions support. Instructs the Online Responder to inspect and process an Online Certificate Status Protocol (OCSP) request that includes a nonce extension. If a nonce extension is included in the OCSP request and this option is selected, the Online Responder will ignore any cached OCSP response and will create a new response that includes the nonce provided in the request. If this option is disabled and a request that includes a nonce extension is received, the Online Responder will reject the request with an "unauthorized" error.
- And the article also states (Which I think is a bit odd; why do you implement NONCE at all then??). But hence the fact that NONCE is disabled.
The Microsoft OCSP client does not support the nonce extension.
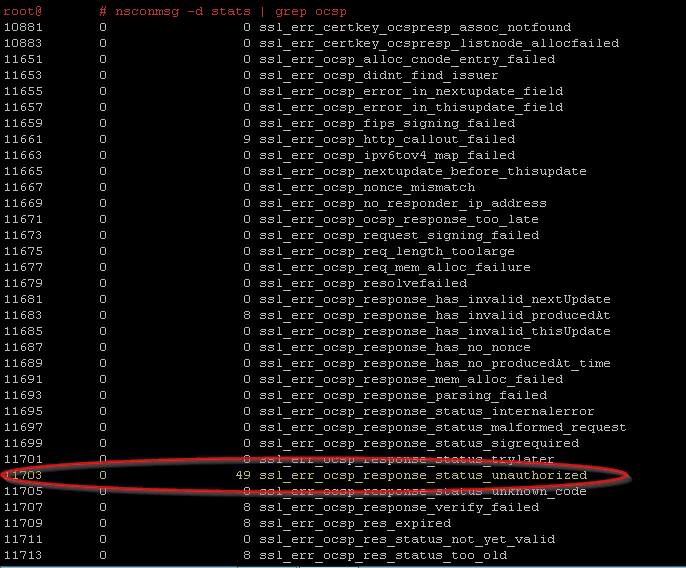
- In a SSH session (shell) the nsconmsg -d stats | grep ocsp shows exactly that
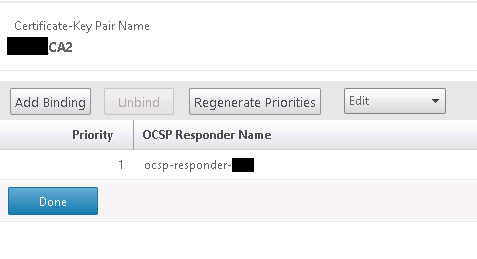
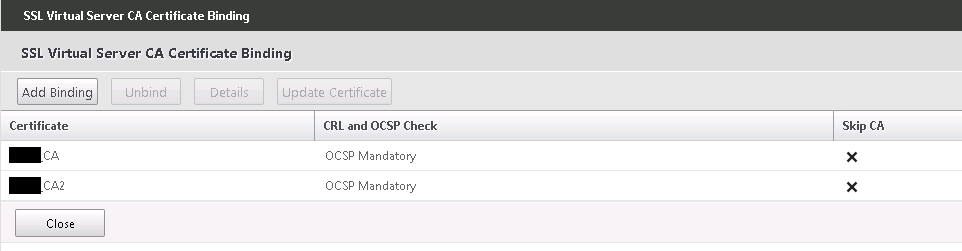
- If you’ve got a CA and intermediate CA, link the OCSP responder to both under SSL certificates with priority one
- If you’ve got a CA and intermediate CA, link both certificates in the Enable Device Certificate on your Vserver
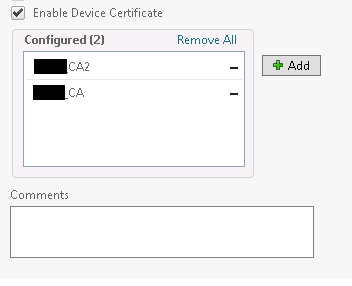
- If you’ve got a CA and intermediate CA, add both to the Basic settings on your Vserver gateway and add both to the certificate section with both mandatory check.
- Add port 80 (bidirectional) for the SNIP address on your firewall (although many google results mention it should be NSIP, a netstat -b on the MS Online Responder server showed me the SNIP address bound to ocspsrv.exe)
This setup made it working for me. Hope it works for you as well.
Leave a Reply to EUC Weekly Digest – June 18, 2016 – Carl Stalhood Cancel reply